Table of contents
- Lab Steps
- Task 1: Sign in to AWS Management Console
- Task 2: Creating a new VPC
- Task 3: Creating and attaching an Internet gateway
- Task 4: Creating two Subnets
- Task 5: Creating Route tables, configuring routes and associating them with Subnets
- Task 6: Creating Security Group
- Task 7: Creating and configuring Network ACL
- Task 8: Launching 2 EC2 Instances
- Task 9: Testing the EC2 instances
- Task 10 : Validation of the Lab
- Completion and Conclusion
- End Lab
Lab Steps
Task 1: Sign in to AWS Management Console
Click on the Open Console button, and you will get redirected to AWS Console in a new browser tab.
On the AWS sign-in page,
Leave the Account ID as default. Never edit/remove the 12 digit Account ID present in the AWS Console. otherwise, you cannot proceed with the lab.
Now copy your User Name and Password in the Lab Console to the IAM Username and Password in AWS Console and click on the Sign in button.
Once Signed In to the AWS Management Console, Make the default AWS Region as US East (N. Virginia) us-east-1.
Note: There is no Validation function for this lab.
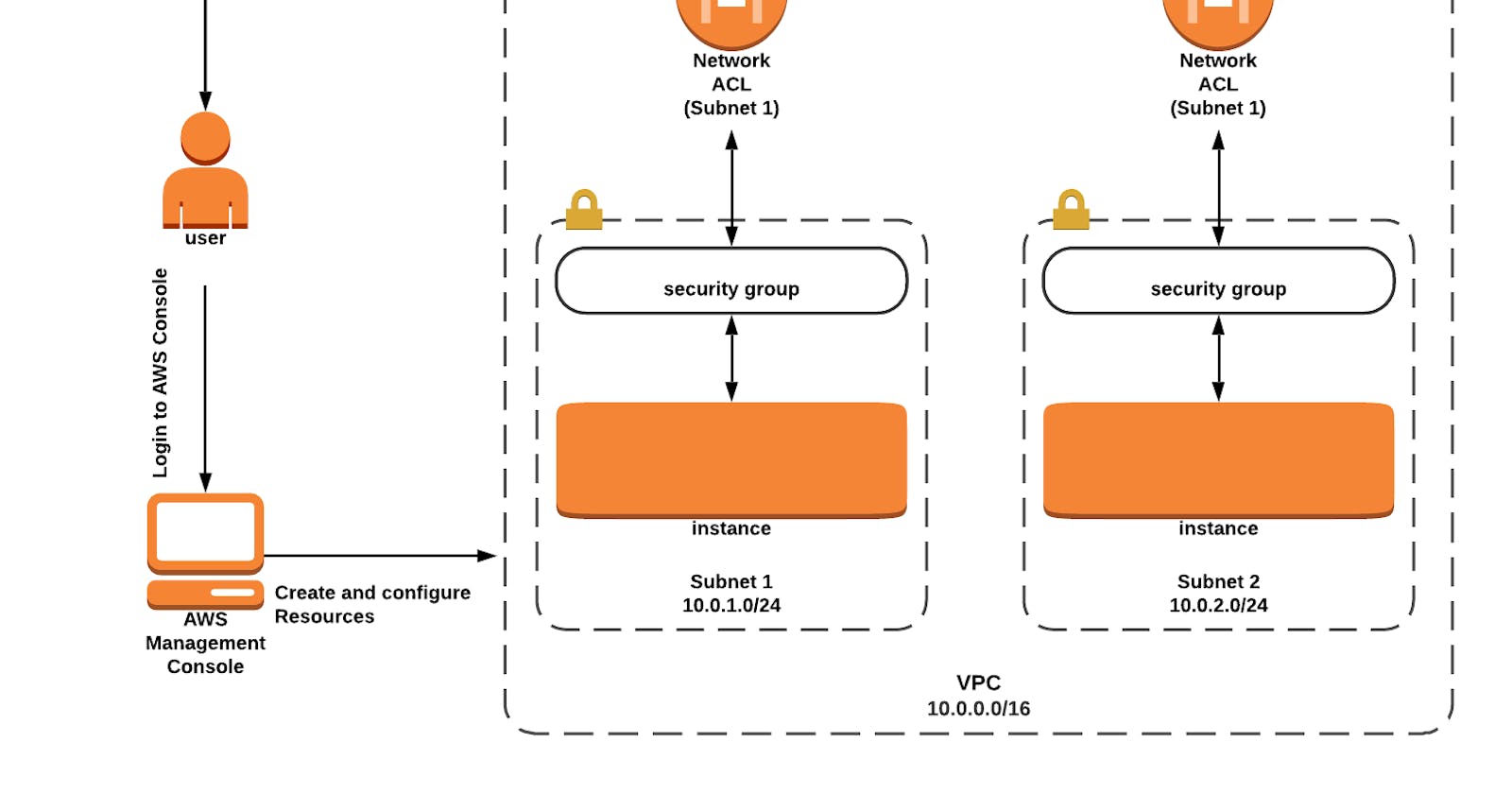
Task 2: Creating a new VPC
In this task, we are going to create a new VPC with the required configurations such as name, IPv4 CIDR block.
Make sure to choose the N.Virginia region in the AWS Management Control dashboard, which is present in the top right corner.
Navigate and click on VPC which will be available under the Networking & Content Delivery section of Services
Click on Your VPCs from the left menu and Click on Create VPC button.
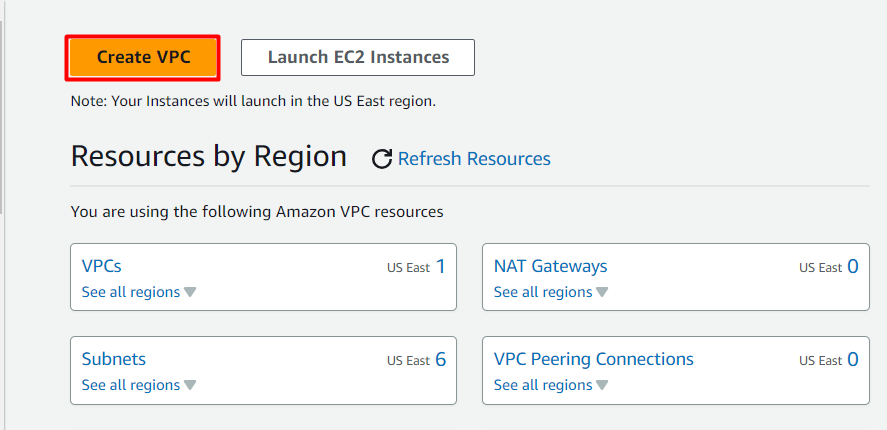
- In Create VPC page fill the following details,
Select VPC Only
Name tag: Enter whizlabs_VPC
IPV4 CIDR Block: Enter 10.0.0.0/16
IPV6 CIDR block: Select No IPV6 CIDR block
Tenancy: Default
Click on Create VPC button.
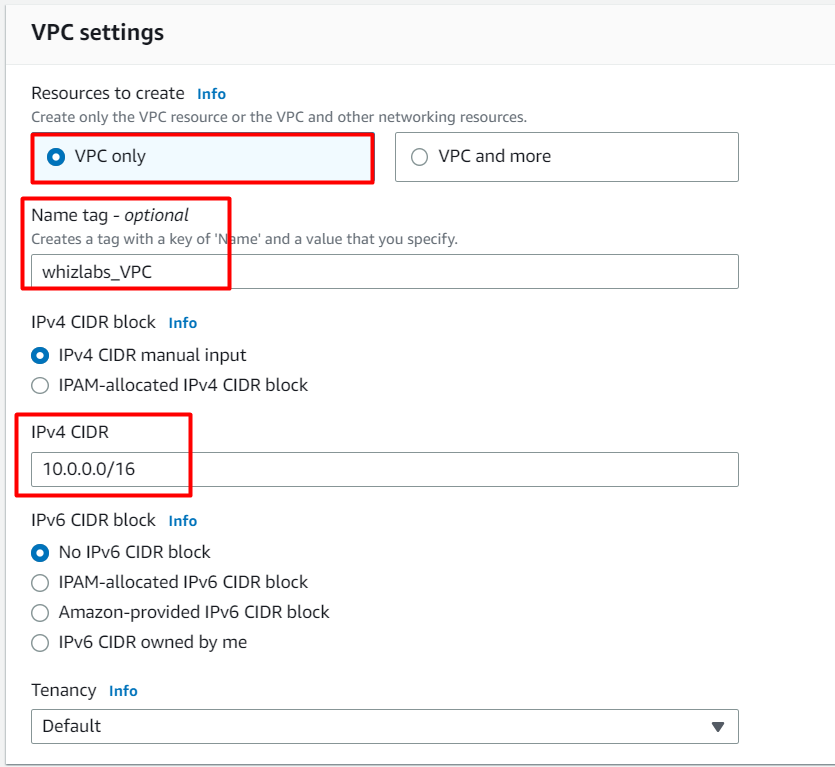
Task 3: Creating and attaching an Internet gateway
In this task, we are going to create an internet gateway and will attach it to the created VPC.
- Click on Internet Gateways from the left menu and click on Create internet gateway button and enter the following details:
Name tag: Enter whizlabs_IGW
Click on Create internet gateway button.
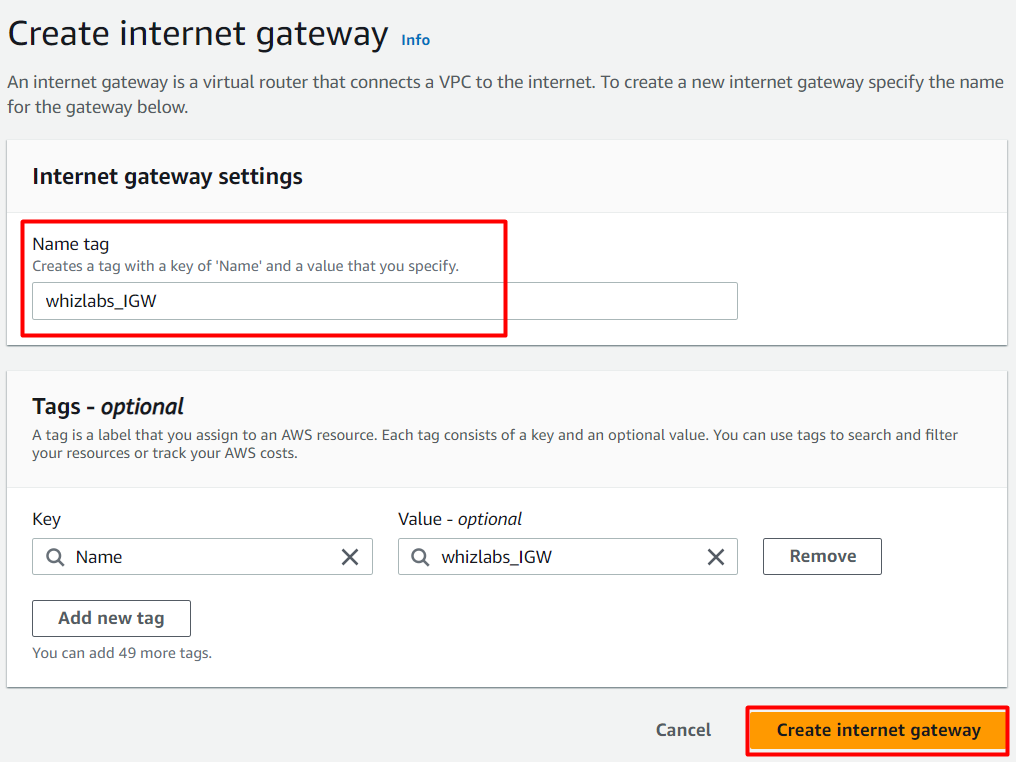
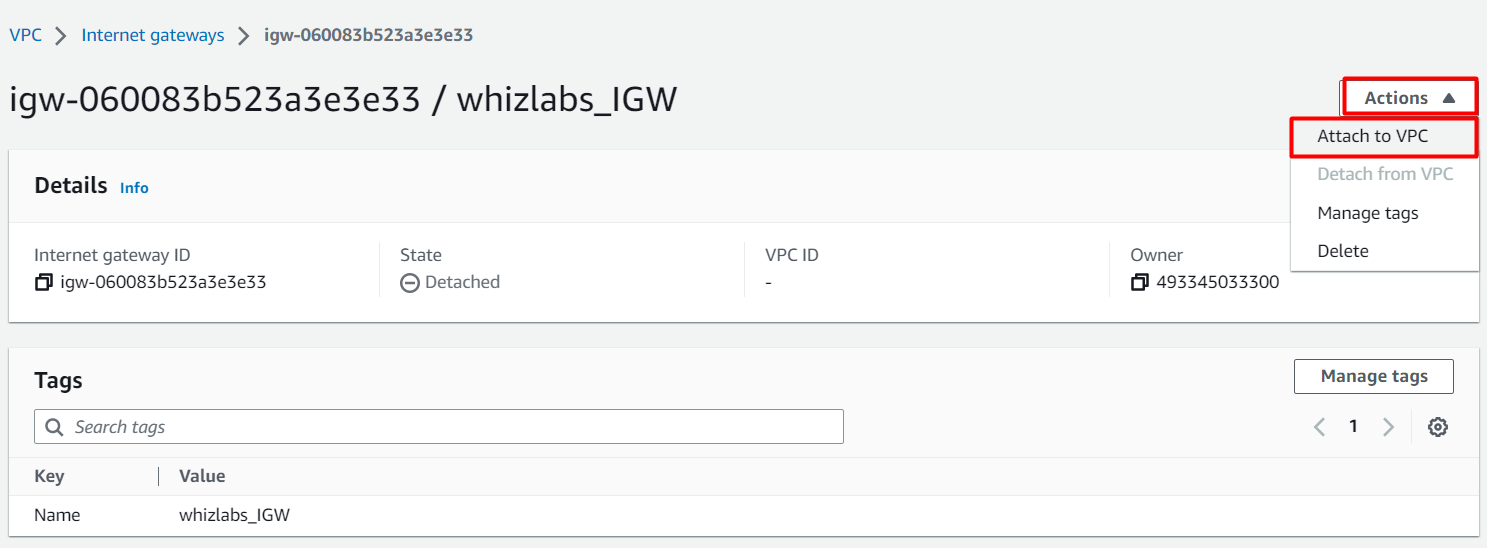
- Select the Internet gateway you created from the list.
Click on Actions button.
Click on Attach to VPC button.
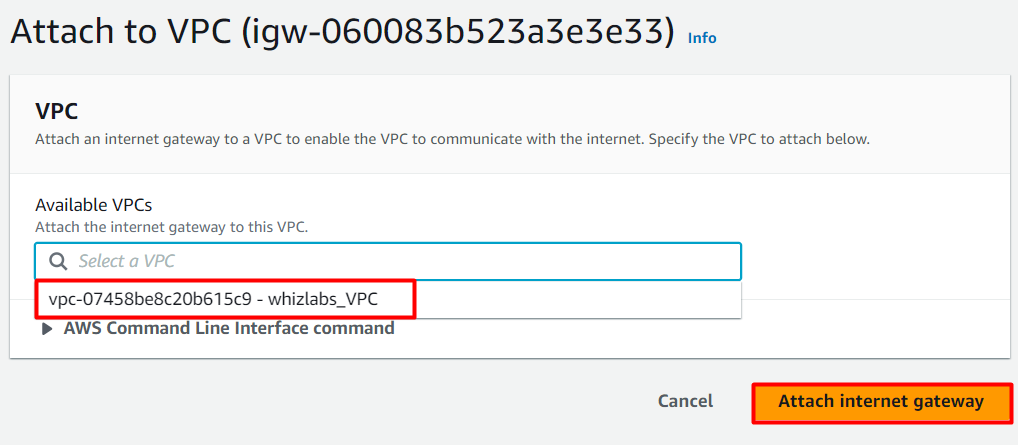
- Select MyVPC from the drop-down and click on Attach internet gateway button.
Task 4: Creating two Subnets
You will create 2 Subnets, one for public and another for private resources. First, we will create a public subnet.
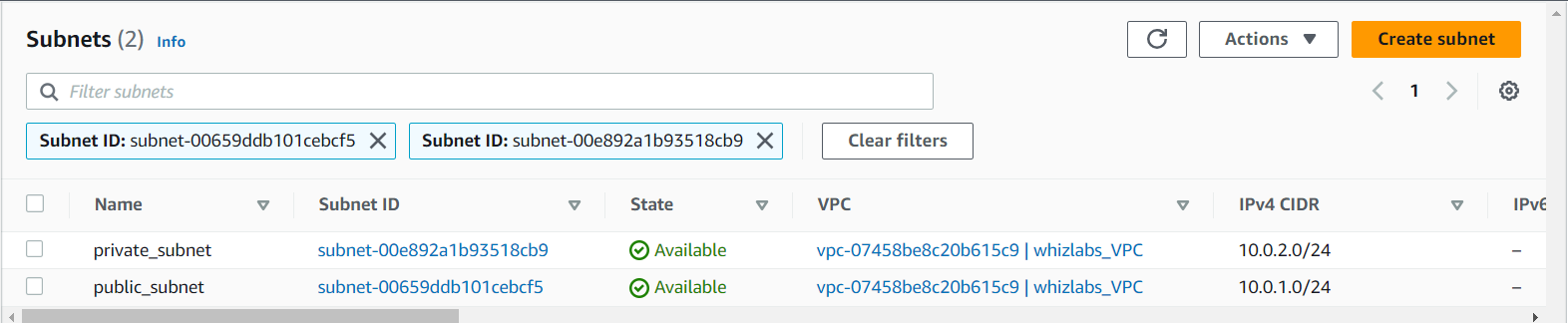
For the Public Subnet, click on Subnets from the left menu and click on Create subnet button.
VPC ID: Select whizlabs_VPC (Select the VPC which you created from the dropdown)
Name tag: Enter public_subnet
Availability zone: Select No Preference
IPv4 CIDR block: Enter 10.0.1.0/24
Click on Create subnet button
- For Private Subnet, click on Create Subnet again.
VPC ID: Select whizlabs_VPC (Select the VPC which you created from the dropdown)
Name tag: Enter private_subnet
Availability zone: Select No Preference
IPv4 CIDR block: Enter 10.0.2.0/24
Click on Create subnet button.
Task 5: Creating Route tables, configuring routes and associating them with Subnets
You will create 2 route tables, one for public routes and another for private routes.
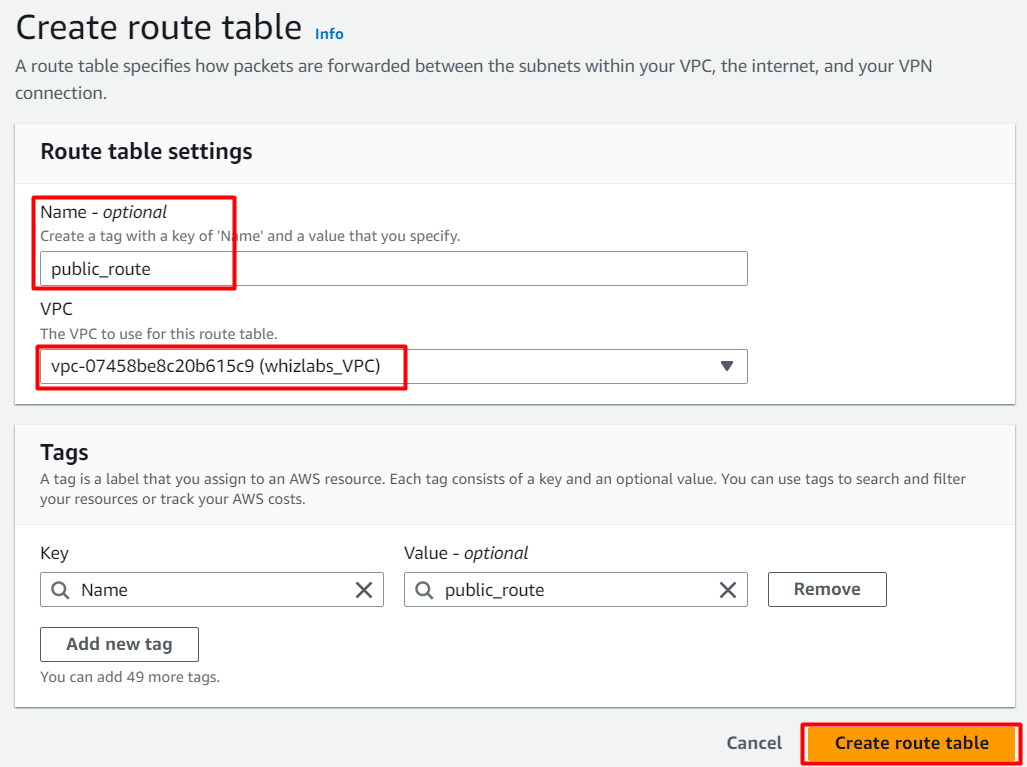
Go to Route Tables from the left menu and click on Create route table button.
Name tag: Enter public_route
VPC: Select whizlabs_VPC (Select the VPC you created from the dropdown)
Click on Create route table button.
- Similarly, go to Route Tables from the left menu and click on Create route table.
Name tag: Enter private_route
VPC: Select whizlabs_VPC (Select the VPC you created from the dropdown)
Click on Create route table button.
- Now, you need to add routes to the Route Tables.
Select public_route.
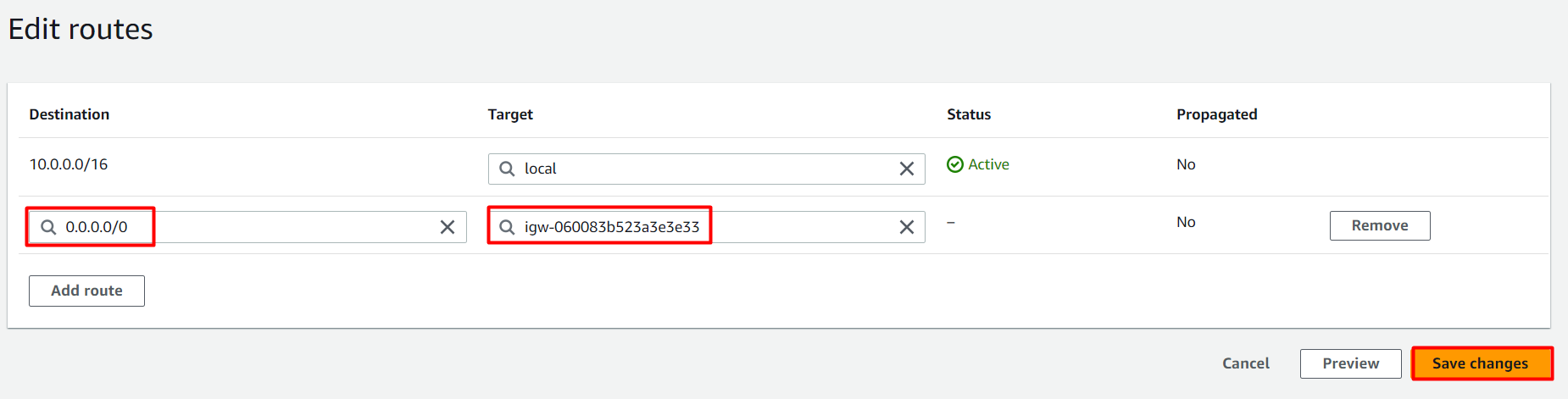
Go to the Routes tab. Click on Edit routes. On the next page, click on Add route.
Specify the following values:
Destination: Enter 0.0.0.0/0
Target: Select Internet Gateway from the dropdown menu to select whizlabs_IGW.
Click on Save changes button.
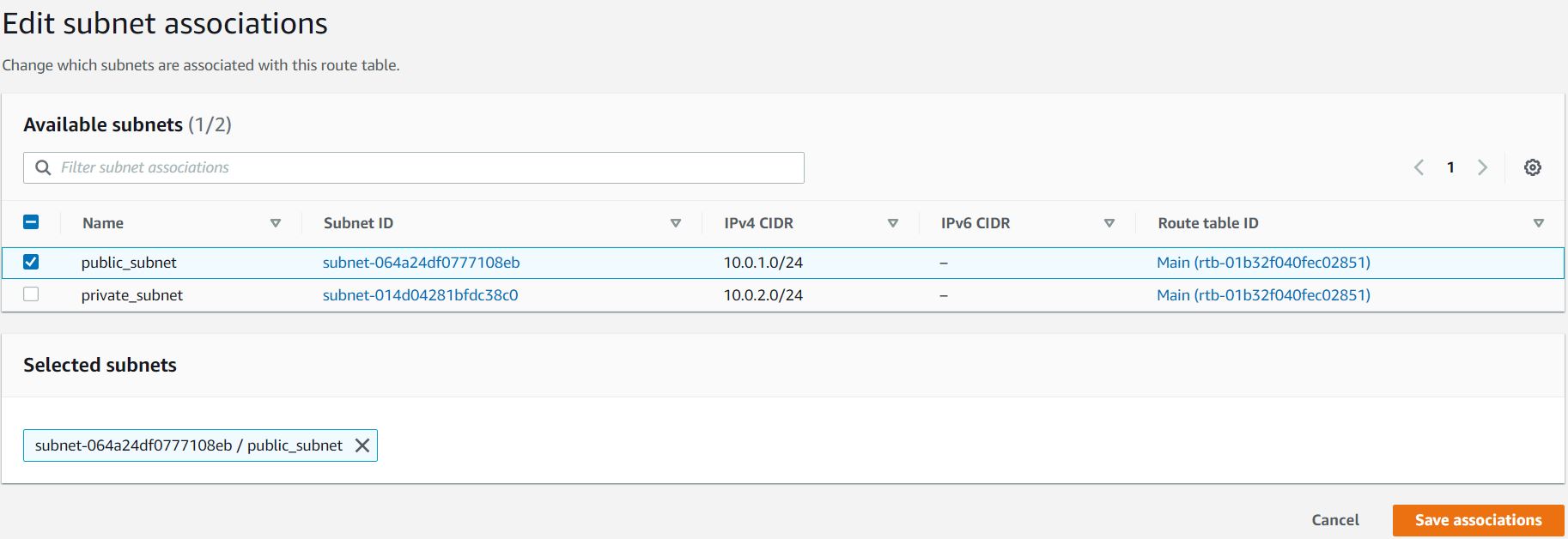
Next, you need to associate the public_subnet with this public_route. Select the public_route and go to the Actions and in that go to Edit Subnet Associations tab.
Click on Edit Subnet Associations.
Select public_subnet from the list.
Click on Save Associations button.
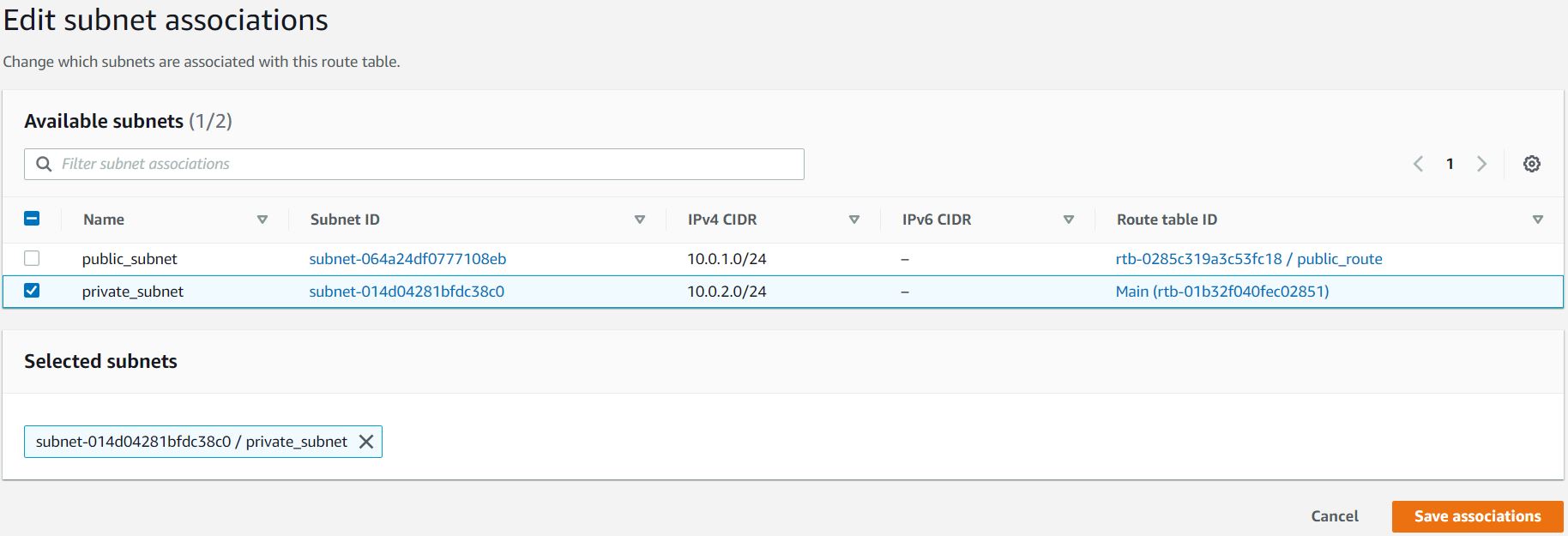
Similarly, you need to associate the private_subnet with this private_route. Select the private_route and go to the Actions and in that go to Edit Subnet Associations tab.
Click on Edit Subnet Associations.
Select private_subnet from the list.
Click on Save Associations button.
Task 6: Creating Security Group
In this task, we are going to create a security group for the EC2 Instance.
- Go to Security Group from the left menu and click on Create security group button and then provide the following details:
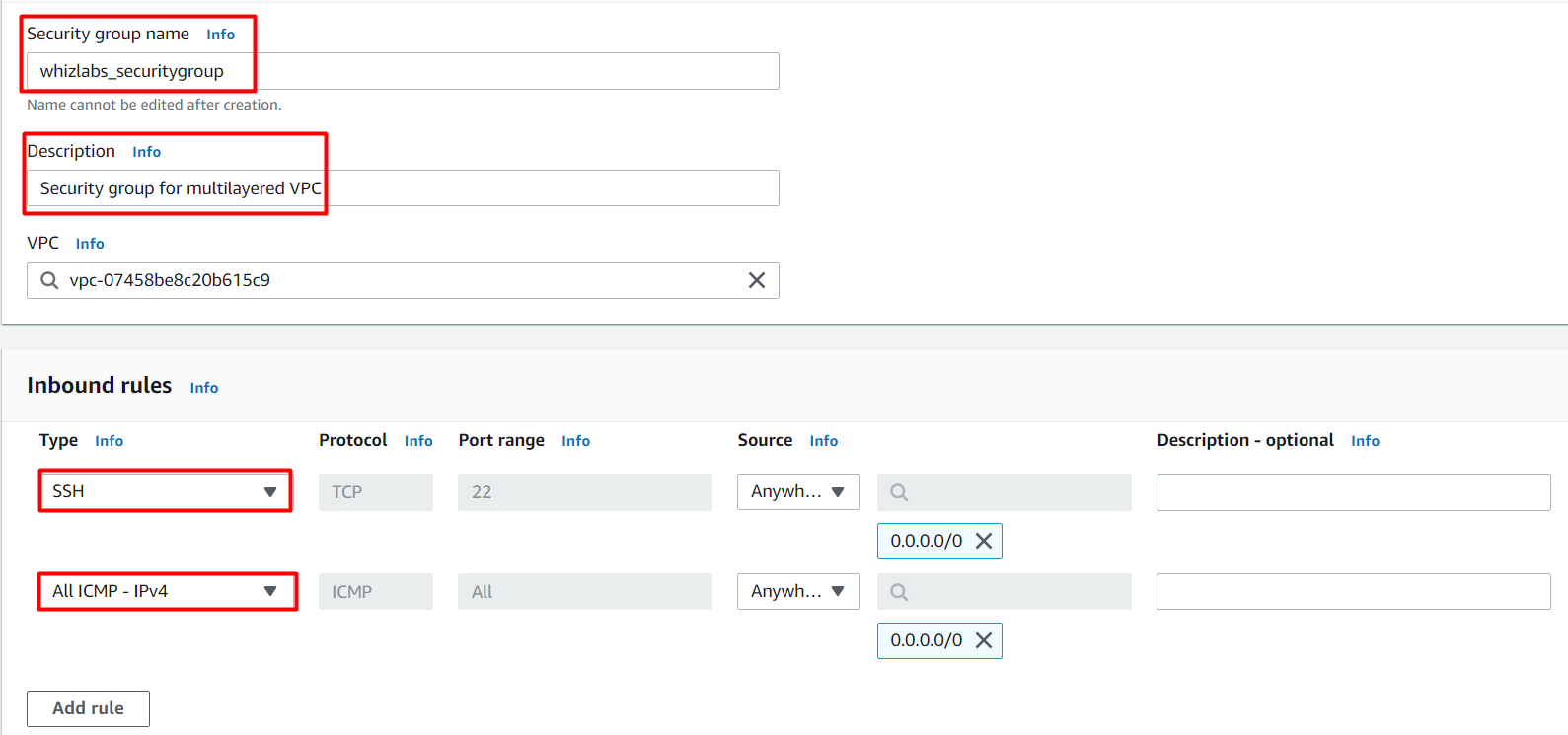
Security group name: Enter whizlabs_securitygroup
Description: Enter Security group for multilayered VPC
VPC: Select whizlabs_VPC (select from the dropdown)
Under Inbound Rules, click on Add Rule button.
To add SSH,
Choose Type: Select SSH
Source: Custom - 0.0.0.0/0
To add All ICMP - IPv4,
Click on Add Rule
Choose Type: Select All ICMP - IPv4
Source: Anywhere IPv4
Click on Create security group button.
Task 7: Creating and configuring Network ACL
Network Access Control Lists (ACLs) in AWS are used to control inbound and outbound traffic at the subnet level. They act as virtual firewalls that provide an additional layer of security for your Amazon Virtual Private Cloud (VPC). In this task, we are going to create and configure Network ACL by adding required inbound and outbound rules.
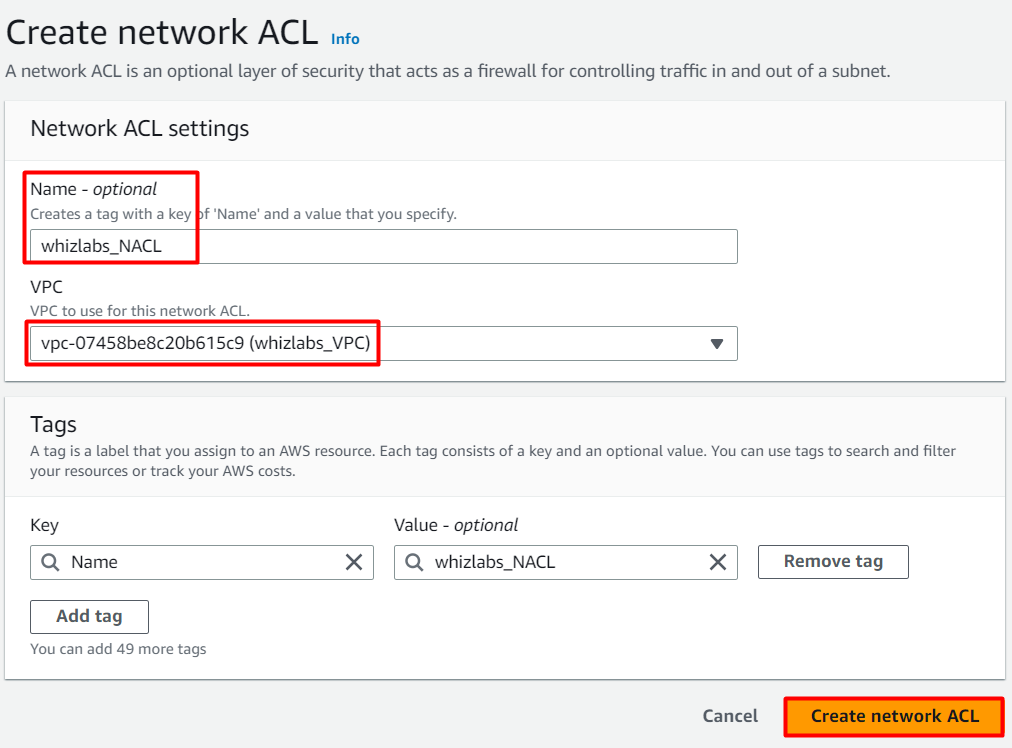
- Go to Network ACLs from the left menu and click on Create network ACL. Provide the following details:
Name tag: Enter whizlabs_NACL
VPC: Select whizlabs_VPC (Select the VPC which you created from the dropdown)
Click on Create network ACL button.
Select whizlabs_NACL and go to Inbound rules tab. Click on Edit inbound rules and then click on the Add new rule.
Add the following rules:
For SSH, click on Add new rule,
Rule number : Enter 100
Type: Choose SSH (22)
Source: Enter 0.0.0.0/0
Allow / Deny: Select Allow
For ALL ICMP- IPv4, click on Add new rule,
Rule number : Enter 200
Type: Choose ALL ICMP - IPv4
Source: Enter 0.0.0.0/0
Allow / Deny: Select Allow
Click on Save changes button.
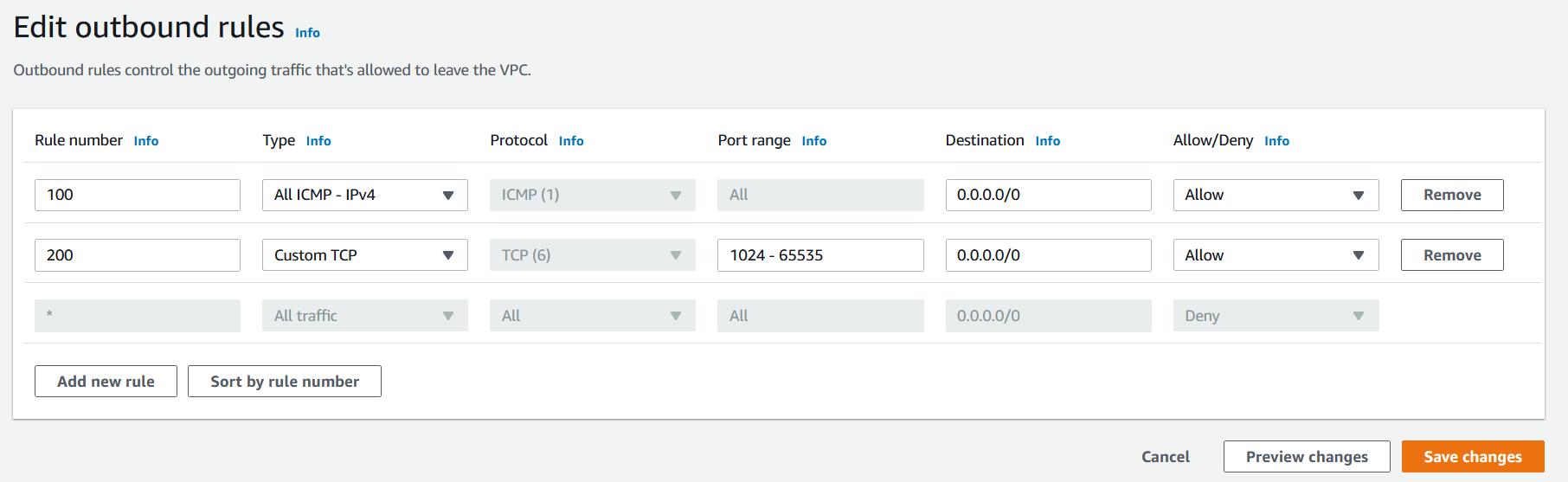
NACLs are stateless. You need to add the rules in Outbound rules too.
Select whizlabs_NACL and go to Onbound rules tab. Click on Edit onbound rules and then click on the Add Rule button.
For ALL ICMP- IPv4, click on Add new rule,
Rule# : Enter 100
Type: Choose ALL ICMP - IPv4
Destination: Enter 0.0.0.0/0
Allow / Deny: Select Allow
For Custom TCP Rule, click on Add new rule,
Rule# : Enter 200
Type: Choose Custom TCP Rule
Port Range: Enter 1024 - 65535
Destination: Enter 0.0.0.0/0
Allow / Deny: Select Allow
Click on Save changes button.
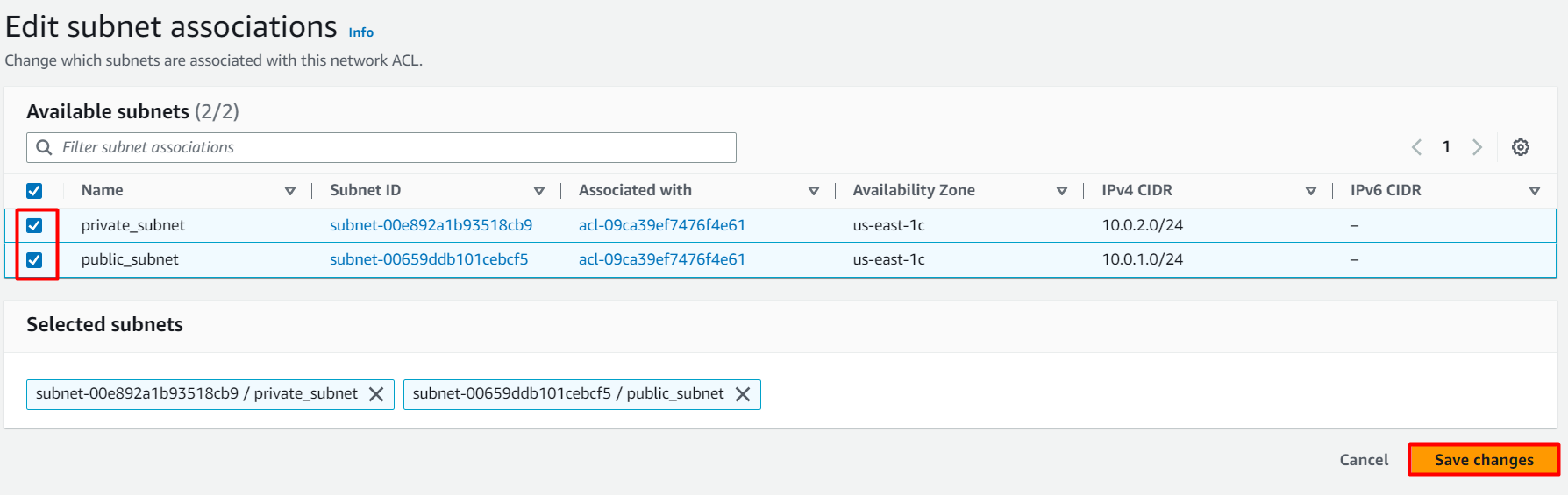
You need to associate both public and private subnets with the NACL.
Select whizlabs_NACL and go to the Subnet associations tab. Click on Edit subnet associations.
Choose all the available subnets and then click on Save changes button.
Task 8: Launching 2 EC2 Instances
Navigate to Services and choose EC2 under Compute
Navigate to Instances on the left panel and click on Launch Instances button.
Name : Enter public_instance
For Amazon Machine Image (AMI): Search for Amazon Linux 2 AMI in the search box and click on the select button.
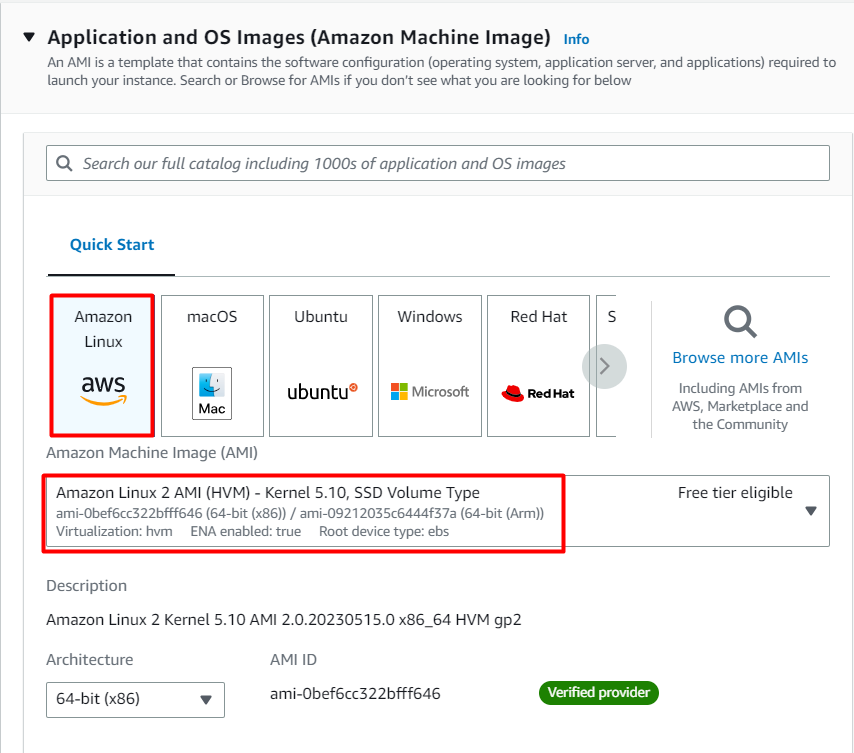
- Note: if there are two AMI's present for Amazon Linux 2 AMI, choose any of them.
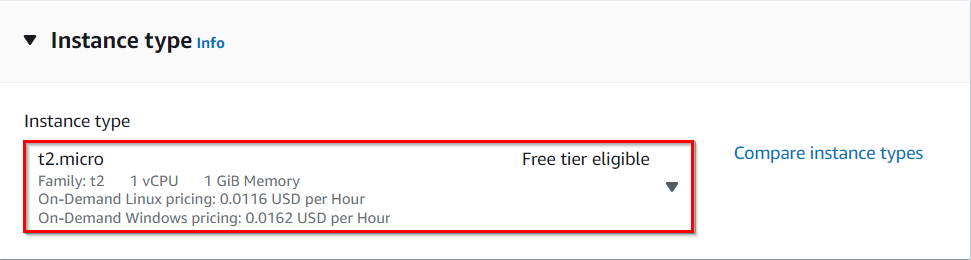
- For Instance Type: Select t2.micro
For Key pair: Select Create a new key pair Button
Key pair name: WhizKey
Key pair type: RSA
Private key file format: .pem
Select Create key pair Button.
In Network Settings Click on Edit button:
VPC: Select whizlabs_VPC
Subnet: Select public_subnet
Auto-assign public IP: Enable
Choose Select an existing security group and remove default one then select whizlabs_securitygroup
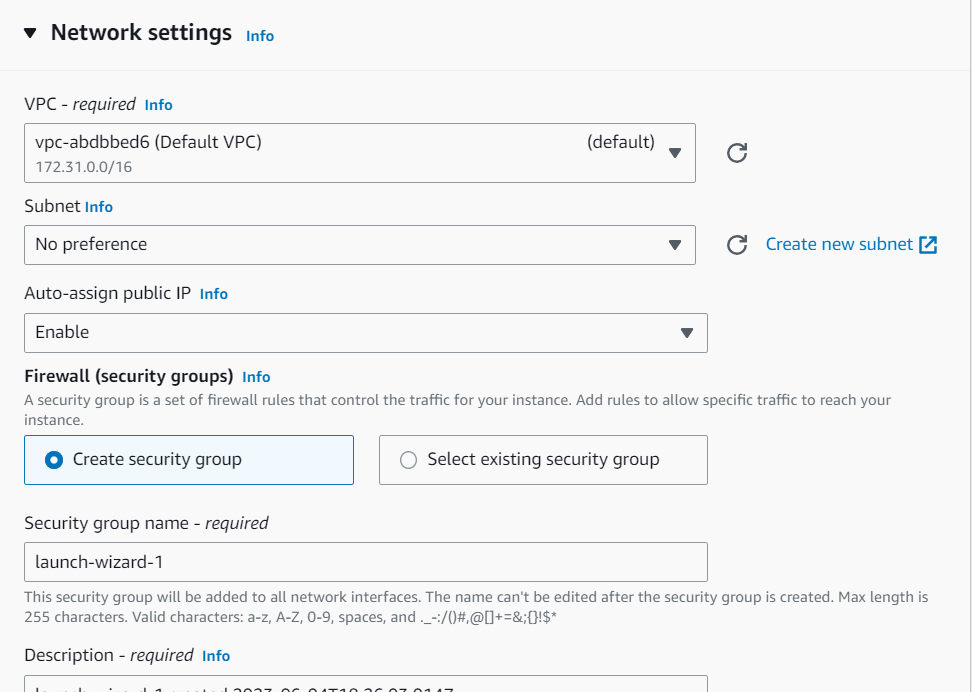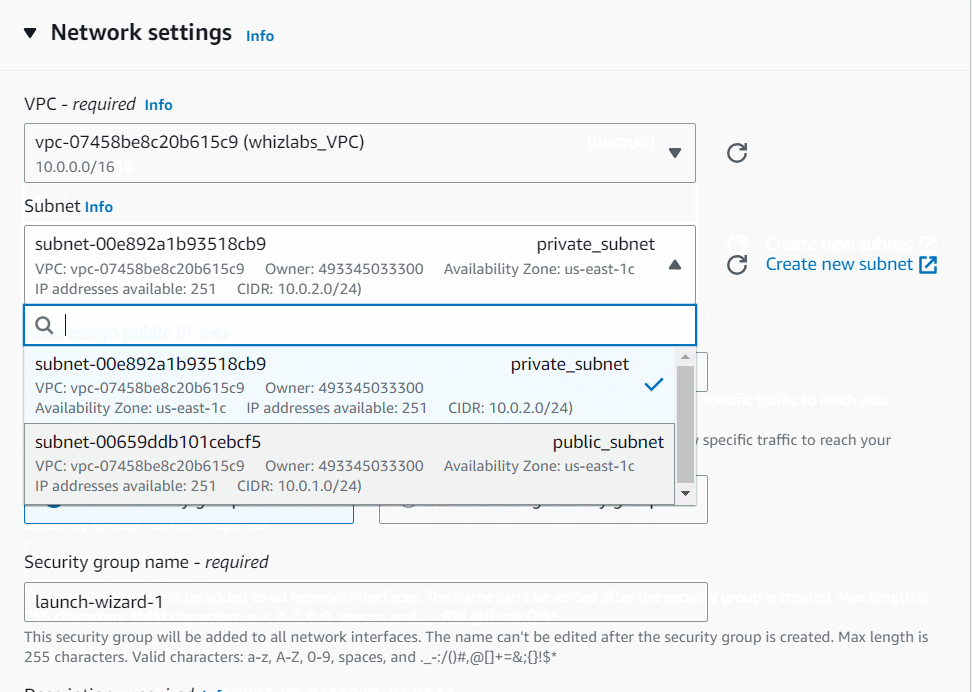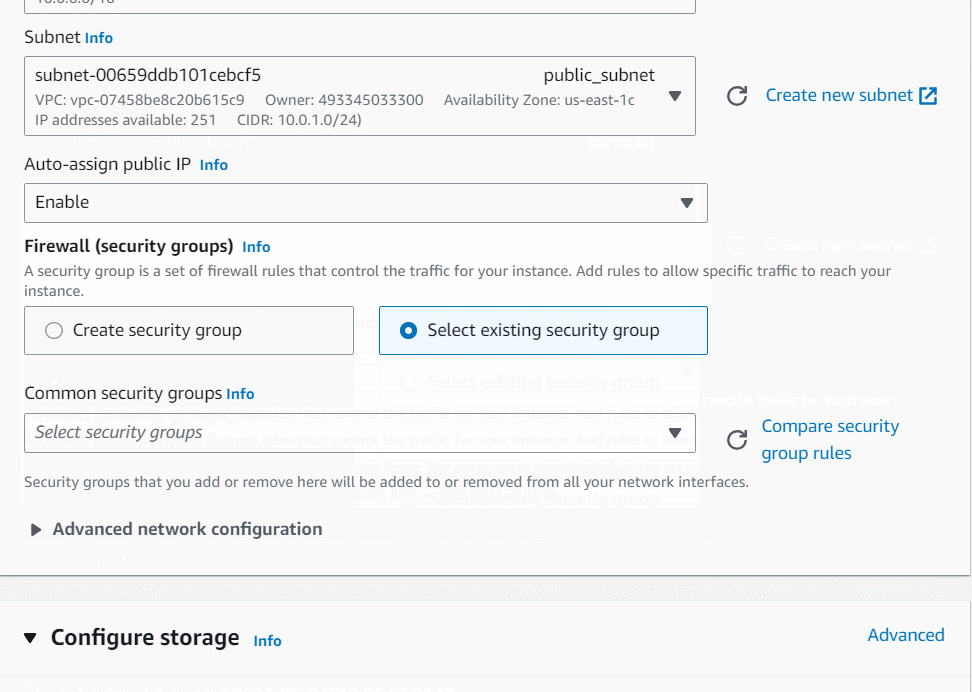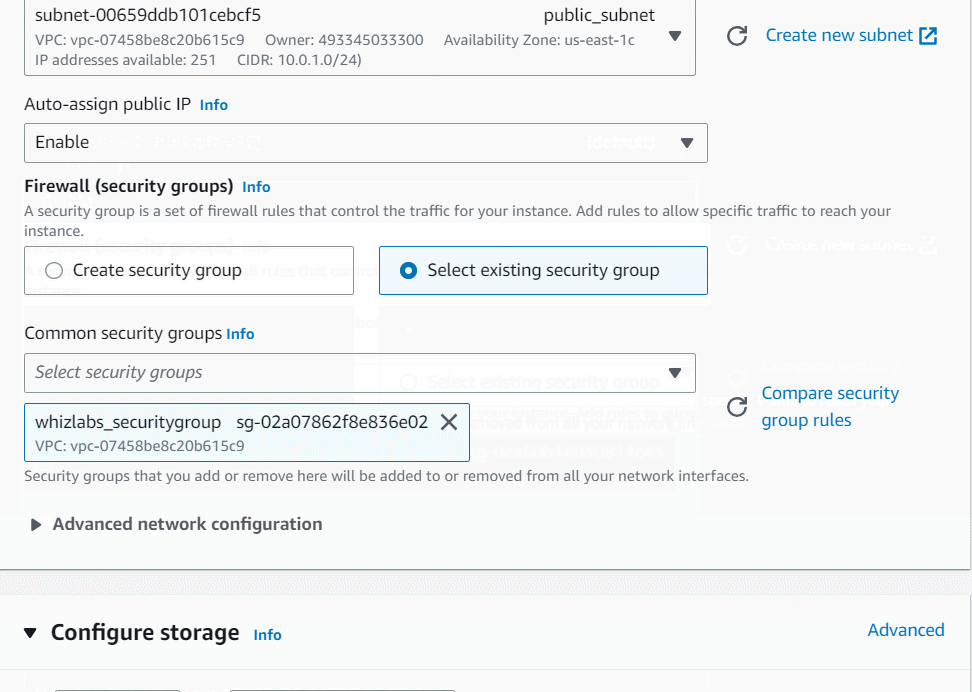
Keep Rest thing Default and Click on Launch Instance Button.
Select View all Instances to View Instance you Created
Similar to the above, launch another EC2 instance:
Name the instance as private_instance
Key pair : Select the existing one
VPC: Select whizlabs_VPC
Subnet: Select private_subnet
Auto-assign public IP: Disable
Choose Select an existing security group and remove default one then select whizlabs_securitygroup
Keep Rest thing Default and Click on Launch Instance Button.
Select View all Instances to View Instance you Created.
Task 9: Testing the EC2 instances
- Select the publc_instance from the EC2 dashboard and copy the public IPv4 address.
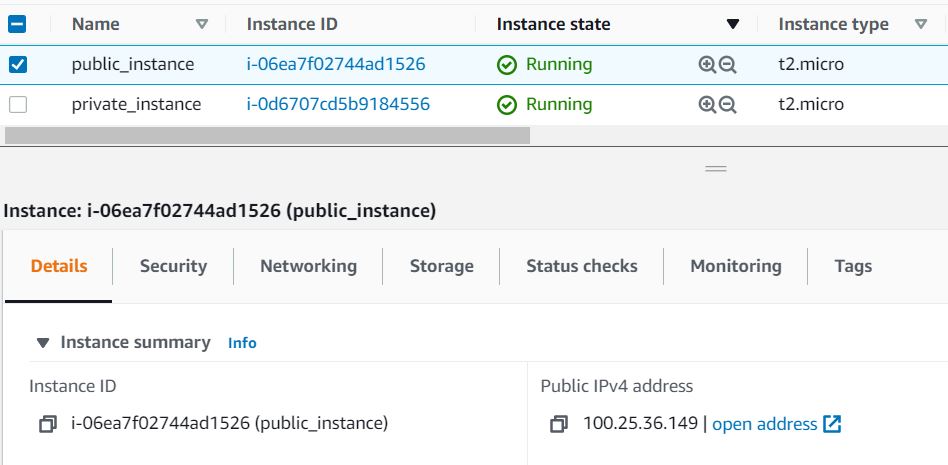
Similarly, copy the Private IPv4 Address of the private_instance.
SSH into public_instance EC2 Instance.
- Please follow the steps in SSH into EC2 Instance.
Ping the private IP of your private_instance by using the below command:
- ping <your Private EC2 IPv4 address>
Once you execute this command, you will receive a response from the IP.
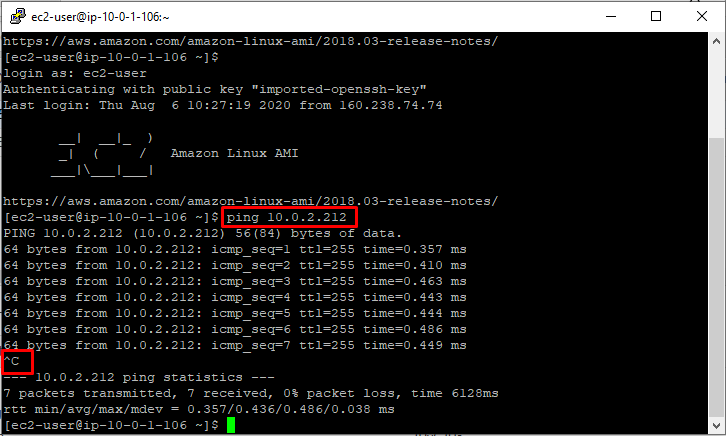
- Press [Ctrl] + C to cancel the process.
Do you know?
Security groups are applied at the instance level and provide stateful control over traffic, while NACLs are applied at the subnet level and provide stateless control over traffic.
Task 10 : Validation of the Lab
Once the lab steps are completed, please click on the Validation button on the left side panel.
This will validate the resources in the AWS account and displays whether you have completed this lab successfully or not.
Sample output :
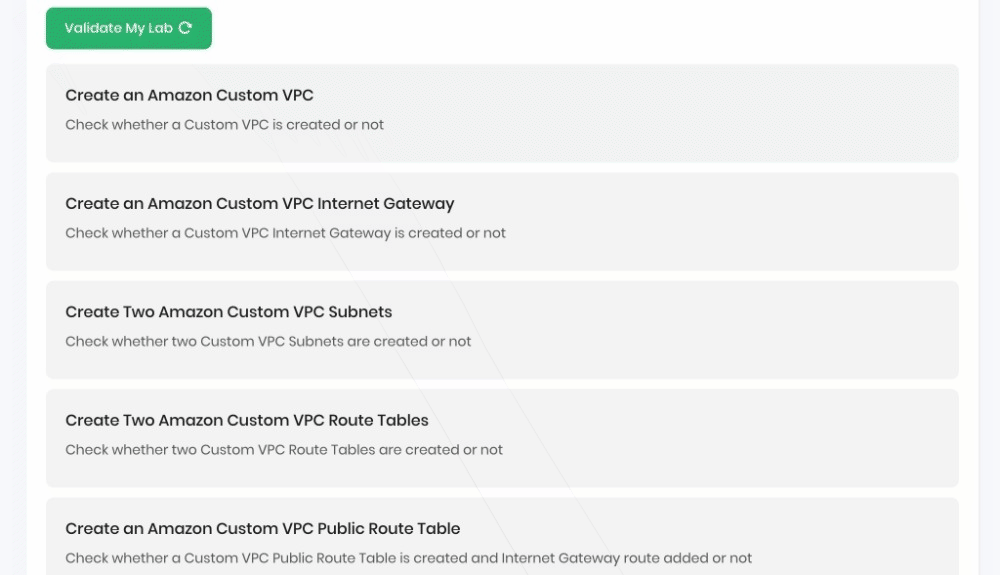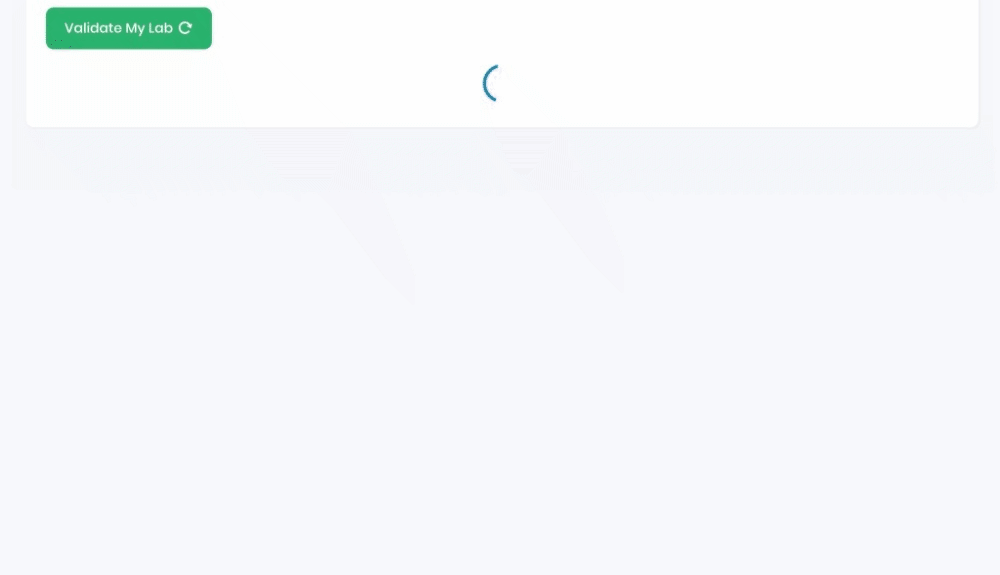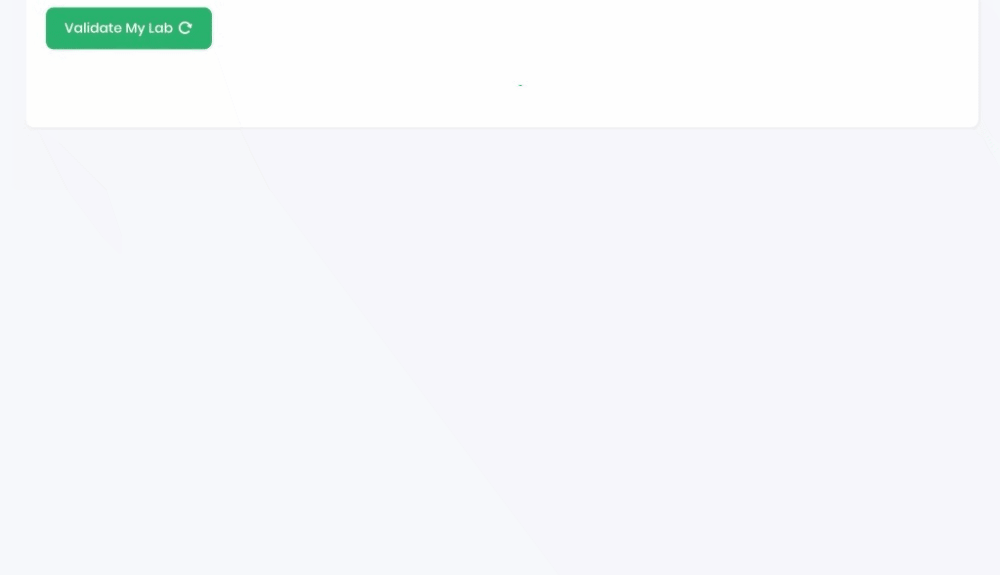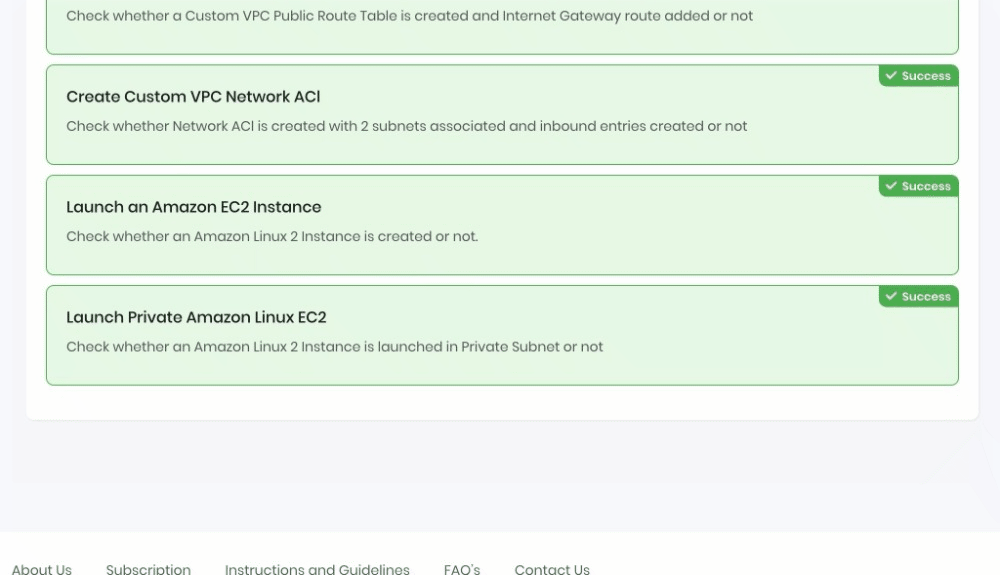
Completion and Conclusion
You have successfully created a new VPC.
You have successfully created and attached an Internet Gateway.
You have successfully created two subnets for public and private AWS instances.
You have successfully created and configured the Route Table.
You have successfully created a Security Group.
You have successfully created and configured Network ACL.
You have successfully launched 2 EC2 instances (one in a public subnet and one in a private subnet).
You have successfully tested the EC2 instance.
End Lab
Sign out from the AWS Account.
You have successfully completed the lab.