Table of contents
- 🌐 What is IaC?
- ⚙️ Terraform
- 📝 Terraform Plan, Apply, Destroy:
- 🔍 Vulnerability Scanning with CSPM
- 🎯 Importance of Shift Left Security
- 🔒 Introduction to Checkov
- 🛠️ Integrating Checkov into Harness Pipeline
- 🔐 Shifting Checkov Scanning Left
- 🚀 Benefits of Left Shift Security
- 👥 Enhanced Collaboration
- 🏗️ Infra as Code & Security
- 🔑 Key Takeaway
In the dynamic realm of software development, Infrastructure as Code (IaC) emerges as a pivotal practice, automating infrastructure provisioning. Let's delve into IaC, Terraform, vulnerability scanning via CSPM, and the significance of Shift Left Security. We'll explore Checkov, its integration into Harness pipelines, pre-commit usage, and its IDE plugin.
🌐 What is IaC?
IaC empowers developers and ops to manage infrastructure via code. This fosters repeatability, consistency, and collaboration, pivotal in DevOps and DevSecOps.
⚙️ Terraform
Terraform by HashiCorp is a renowned IaC tool, enabling cloud-agnostic infrastructure management with its declarative approach.
📝 Terraform Plan, Apply, Destroy:
terraform plan: Generates a plan for desired state.
terraform apply: Executes planned changes.
terraform destroy: Removes resources.
🔍 Vulnerability Scanning with CSPM
Cloud Security Posture Management (CSPM) tools, like Scoutsuite, scan cloud resources for security risks.
🎯 Importance of Shift Left Security
Integrating security early mitigates risks, enhancing efficiency and cost-effectiveness.
🔒 Introduction to Checkov
Checkov, a static analysis tool, identifies IaC security risks before resource creation, supporting Terraform, CloudFormation, Kubernetes YAML, and more.
🛠️ Integrating Checkov into Harness Pipeline
Harness seamlessly integrates Checkov scans, ensuring only secure code is deployed.
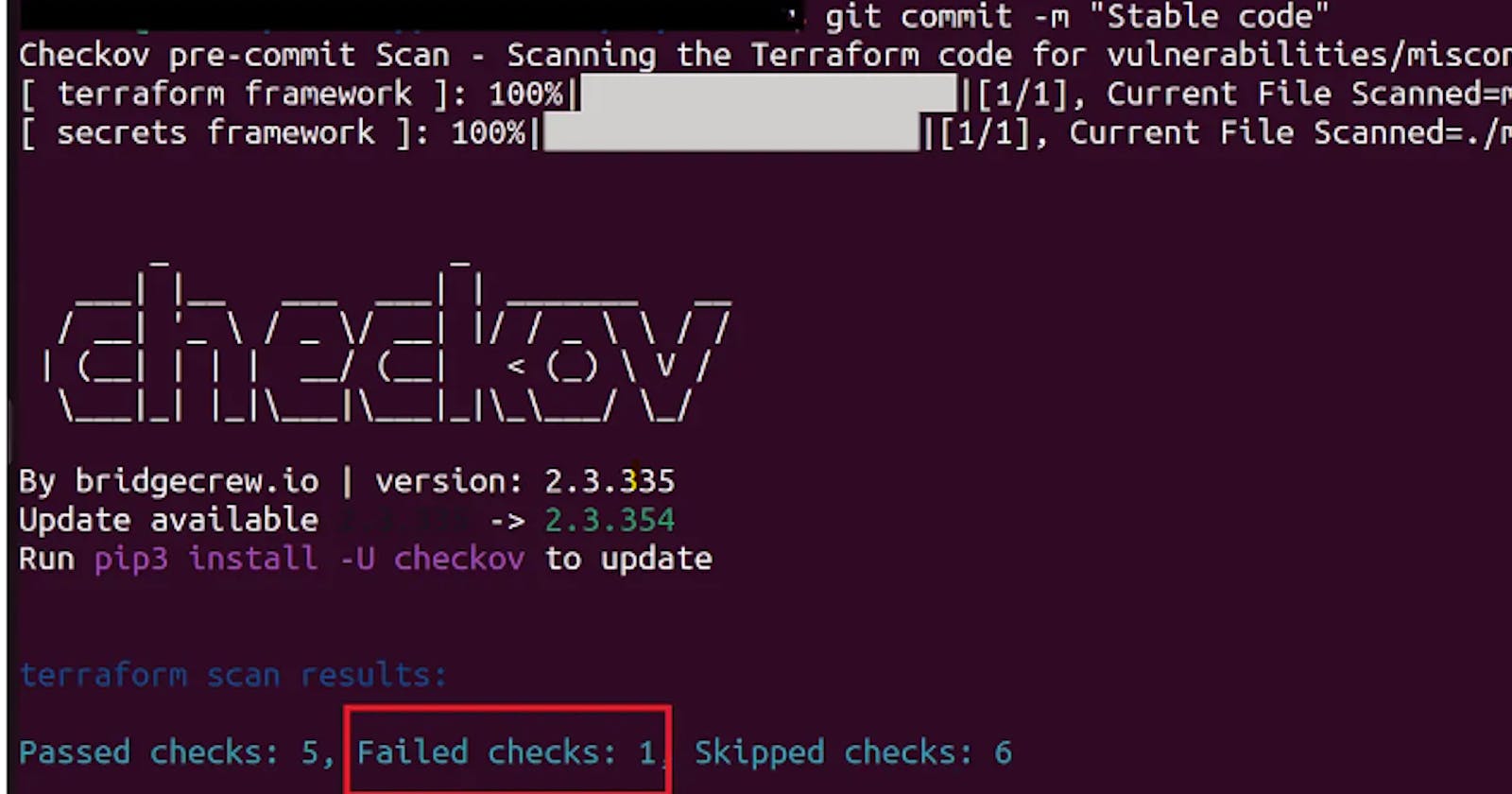
🔐 Shifting Checkov Scanning Left
Pre-Commit: Real-time Checkov scans during code commit.
IDE Plugin: Immediate feedback on vulnerabilities while coding.
🚀 Benefits of Left Shift Security
Immediate feedback loop.
Early detection & remediation.
Reduced costs & risks.
Proactive approach & compliance.
👥 Enhanced Collaboration
Shift Left Security fosters better teamwork between development, operations, and security teams.
🏗️ Infra as Code & Security
These practices empower secure, efficient, and collaborative software deployment. Tool choices should align with team needs and goals.
🔑 Key Takeaway
Shift Left Security, IaC, and Checkov champion secure software development, enhancing efficiency and robustness.